Researchers at Perception Point have come across a new multi-step infostealer malware campaign that hackers use to breach the systems of hotels, booking sites, and travel agencies. The researchers first discovered these attacks in August, and after finding hotels getting attacked by the same malware, they decided to investigate further. The malware campaign was launched through an exceptionally well-crafted and sophisticated pushing technique, exploiting the hotels and booking.com system to go after the consumer’s financial information.
These attacks happened for a week across the globe, targeting major countries like Spain, Germany, and Israel, specifically in the peak tourist season. A successful attack like this could result in damages of millions of dollars.
The modern phishing attack- technical insights.
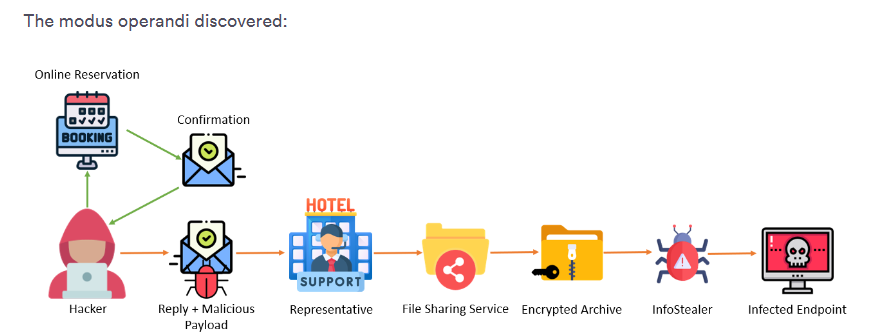
The infostealer malware spread and targeted consumers through a sophisticated and well-engineered phishing attack, which, according to the Perception Point spokesperson, is “almost like a spear phishing attack.” the most impressive thing about the attack was that it was based on the phisher utilizing the hotel account which made the attack seem legit.
Unlike a traditional phishing attack, it did not rely on smishing or any rogue email. Instead, it started with the threat actors breaching the hotel’s official account on Booking.com. With access to the official account, threat actors now had access to all sensitive customer information, such as:
- Names
- Booking dates
- Hotel Details
- Partial payment methods
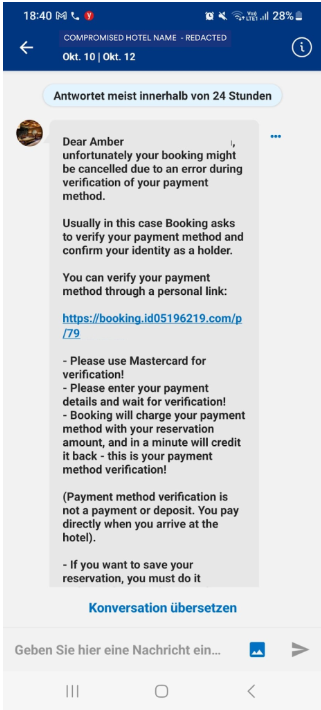
This data is crucial and laid the very foundation of the attack. Proceeding from this, the attackers used this harvested data to craft individual messages, deploying the typical social engineering tactic of instilling panic. Twenty-four hours before arriving at the hotel, the victims received a notification asking them to provide their credit card details as a verification test; otherwise, their booking would be canceled if they failed to comply.
The message was sent to the victims via the booking.com platform and the official booking.com email. It had links that led the victims to a deceptive but well-designed phishing page that came pre-injected with specific information fitting the victims, such as:
- Their name
- The hotel they have booked
- The exact dates of their stay
The personalization of these contents made the message seem legit, ensuring that the customers would respond to it timely. Once the victims re-enter their credit card or bank information, the data is directly harvested by attackers, which would lead to financial fraud.
According to the Perception Point researchers, this campaign parallels a previous campaign targeting travel agencies. This alarming connection indicates a rise in cyber attacks targeting the hospitality sector.
After effects of the attacks- how to stay safe?
According to Perception Point research, the attack was not an isolated incident. Instead, it was rather carefully designed to target thousands of consumers. According to Peleg Cabra, the product marketing manager at Perception Point, the losses from this campaign could be alarming.
“I was impressed by the sophisticated nature of the attack. The losses from this particular campaign will be in millions.”
Since the attack is very well crafted and sophisticated, it means that the threat actors are now evolving. Therefore, it seems that “the battleground has moved from enterprises to scamming the consumer, and where would they do that? Browsers. Browsers should have better phishing detection and prevention techniques. And consumers need to add better security measures around the browsers,” said Peleg
Additionally, researchers at Perception Point also suggested some other vital methods that consumers can use to ensure security, such as:
- Always double-check URLs to ensure they align with the legitimate website. It is important to look for misspellings, unfilial domain extensions, or suspicious and broken links on the webpage.
- Best beware of urgent requests and verify their legitimacy, as phishers induce a false sense of urgency to trick victims
- If they receive suspicious emails, they should contact official contact details instead of those in the email.
Along with that, Peleg also suggested that platforms like Booking.com, hotels, and travel agents should also ensure the safety of their customers in various ways. While the info stealer malware could bypass MFA by stealing cookies, it is still essential to a sound cybersecurity strategy. Therefore, every enterprise should implement it. Moreover, the industries involved in the hospitality sector should also implement better security and detection measures. They should be able to detect any suspicious activities.
Final Words
The sophistication of these modern cyber-attacks means that the cybersecurity threat landscape is set to change drastically. While Booking.com is not the one to blame for the attack, they did take the initiative to notify the victims of the phishing attempt so they could secure their credit card information.